Free Update Windows XP, Vista Spam
We received many spams related to "Official Update 2008!", the content describes free update Windows XP and Vista.
The following screens will be displayed when clicked the link inside email:



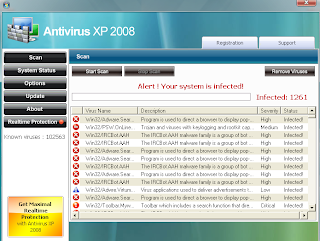
==The following focus on Web Reputation Service Testing==
Google Search CANNOT find it as below:
McAfee SiteAdvisor CANNOT find it as below:
Trend Micro WRS CAN find it as below:
finjan URL analysis CANNOT find it as below:
Dr.Web URL analysis CAN find it as below:
Exploit Prevention Labs's LinkScanner CANNOT find it as below:
Symantec Safe Web CAN find it as below:
==The following focus on AV Scanners Testing==
File install.exe received on 08.28.2008 04:20:46 (CET)
Antivirus Version Last Update Result
AhnLab-V3 2008.8.27.1 2008.08.27 -
AntiVir 7.8.1.23 2008.08.27 -
Authentium 5.1.0.4 2008.08.28 W32/FakeAV2008.AT
Avast 4.8.1195.0 2008.08.27 -
AVG 8.0.0.161 2008.08.27 Downloader.FraudLoad.N
BitDefender 7.2 2008.08.28 Trojan.FakeAlert.ACE
CAT-QuickHeal 9.50 2008.08.26 (Suspicious) - DNAScan
ClamAV 0.93.1 2008.08.28 -
DrWeb 4.44.0.09170 2008.08.27 Trojan.Packed.619
eSafe 7.0.17.0 2008.08.27 Suspicious File
eTrust-Vet 31.6.6052 2008.08.27 -
Ewido 4.0 2008.08.27 -
F-Prot 4.4.4.56 2008.08.28 W32/FakeAV2008.AT
F-Secure 7.60.13501.0 2008.08.27 -
Fortinet 3.14.0.0 2008.08.27 -
GData 19 2008.08.28 Backdoor.Win32.Frauder.bi
Ikarus T3.1.1.34.0 2008.08.28 Trojan-Downloader.Win32.Renos.AS
K7AntiVirus 7.10.428 2008.08.25 -
Kaspersky 7.0.0.125 2008.08.28 Backdoor.Win32.Frauder.bi
McAfee 5371 2008.08.27 Downloader-ASH.gen.b
Microsoft 1.3807 2008.08.25 -
NOD32v2 3394 2008.08.27 a variant of Win32/Kryptik.E
Norman 5.80.02 2008.08.27 W32/Tibs.gen225
Panda 9.0.0.4 2008.08.27 -
PCTools 4.4.2.0 2008.08.27 -
Prevx1 V2 2008.08.28 Malicious Software
Rising 20.59.21.00 2008.08.27 -
Sophos 4.33.0 2008.08.28 -
Sunbelt 3.1.1582.1 2008.08.26 -
Symantec 10 2008.08.28 -
TheHacker 6.3.0.6.064 2008.08.27 -
TrendMicro 8.700.0.1004 2008.08.27 -
VBA32 3.12.8.4 2008.08.27 -
ViRobot 2008.8.27.1352 2008.08.27 -
VirusBuster 4.5.11.0 2008.08.27 -
Webwasher-Gateway 6.6.2 2008.08.27 -
Additional information
File size: 203776 bytes
MD5...: 0f44ed00c0b67d9e5062b8e2c3574345
SHA1..: 4d9b42bbd950ea0c253a483ea2db3f888055c1c6
SHA256: e5885411c5ab7dbf2846b3b0606f6b294bbc9203ec8065d13560470ceab07c07
SHA512: b1b437a2df0023e1af019e6a06c31d298063f156819ea5b1de4047ad5766c6f8
00db13161056c7db223737cfc8fe00ce58d7756ebe33e4042627d6c9fbee8a6f
PEiD..: -
TrID..: File type identification
Win32 Executable Generic (38.4%)
Win32 Dynamic Link Library (generic) (34.2%)
Clipper DOS Executable (9.1%)
Generic Win/DOS Executable (9.0%)
DOS Executable Generic (9.0%)
PEInfo: PE Structure information
( base data )
entrypointaddress.: 0x40a064
timedatestamp.....: 0x48a5befd (Fri Aug 15 17:38:05 2008)
machinetype.......: 0x14c (I386)
( 4 sections )
name viradd virsiz rawdsiz ntrpy md5
.text 0x1000 0xec3c 0x9800 7.99 173f4b069cad8234c767f5babf94449f
.rdata 0x10000 0x3f24 0x1a00 7.97 f38fb4bec5a8839e5c0bf8002d2251be
.data 0x14000 0xb6736 0x23600 8.00 b45b61b4c432446d3586a20be0fd245f
.rsrc 0xcb000 0xf000 0x3000 6.61 bbb4f98ddad8c83b4433986df95b248c
( 4 imports )
> wsock32.dll: bind, WSAStartup, listen
> kernel32.dll: CreatePipe, TerminateProcess, VirtualProtect
> gdi32.dll: SetRelAbs, StretchBlt, SetICMMode, ResetDCW, UpdateColors, SaveDC, TextOutW, SetDIBColorTable
> shell32.dll: SHAppBarMessage, StrRChrIA, StrStrIA
( 0 exports )
ThreatExpert info: http://www.threatexpert.com/report.aspx?md5=0f44ed00c0b67d9e5062b8e2c3574345
Prevx info: http://info.prevx.com/aboutprogramtext.asp?PX5=5764A358008210271CBA03774D18AA00F10D311C
After executed, it has the following behaviors:
[Added process]
C:\Documents and Settings\Administrator\Desktop\install.exe
C:\WINDOWS\system32\pphcl76j0eg03.exe
C:\Program Files\rhcg76j0eg03\rhcg76j0eg03.exe
[DLL injection]
C:\Program Files\rhcg76j0eg03\msvcr71.dll
[Added file]
C:\Documents and Settings\Administrator\Application Data\Microsoft\Internet Explorer\Quick Launch\Antivirus XP 2008.lnk
C:\Documents and Settings\Administrator\Local Settings\Temp\.ttA6.tmp.vbs
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\13833935xv3[1].swf
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\install[1].exe
C:\Documents and Settings\Administrator\Recent\install.exe.txt.lnk
C:\Documents and Settings\Administrator\Recent\wireshark.cap.lnk
C:\Documents and Settings\All Users\Desktop\Antivirus XP 2008.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Antivirus XP 2008.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\How to Register Antivirus XP 2008.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\License Agreement.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Register Antivirus XP 2008.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Uninstall.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008.lnk
C:\Program Files\rhcg76j0eg03\database.dat
C:\Program Files\rhcg76j0eg03\license.txt
C:\Program Files\rhcg76j0eg03\MFC71.dll
C:\Program Files\rhcg76j0eg03\MFC71ENU.DLL
C:\Program Files\rhcg76j0eg03\msvcp71.dll
C:\Program Files\rhcg76j0eg03\msvcr71.dll
C:\Program Files\rhcg76j0eg03\rhcg76j0eg03.exe
C:\Program Files\rhcg76j0eg03\rhcg76j0eg03.exe.local
C:\Program Files\rhcg76j0eg03\Uninstall.exe
C:\WINDOWS\system32\blphcl76j0eg03.scr
C:\WINDOWS\system32\lphcl76j0eg03.exe
C:\WINDOWS\system32\phcl76j0eg03.bmp
C:\WINDOWS\system32\pphcl76j0eg03.exe
C:\WINDOWS\system32\Restore\MachineGuid.txt
[Added registry]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=lphcl76j0eg03
Data=C:\WINDOWS\system32\lphcl76j0eg03.exe
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=SMrhcg76j0eg03
Data=C:\Program Files\rhcg76j0eg03\rhcg76j0eg03.exe
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\rhcg76j0eg03
Value=DisplayName
Data=AntivirXP08
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\rhcg76j0eg03
Value=UninstallString
Data="C:\Program Files\rhcg76j0eg03\uninstall.exe"
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\rhcg76j0eg03
C:\Doc





































